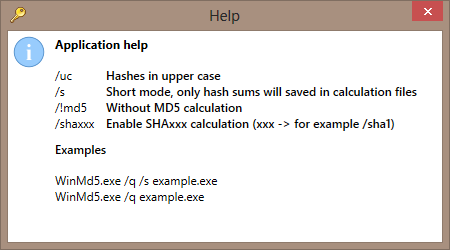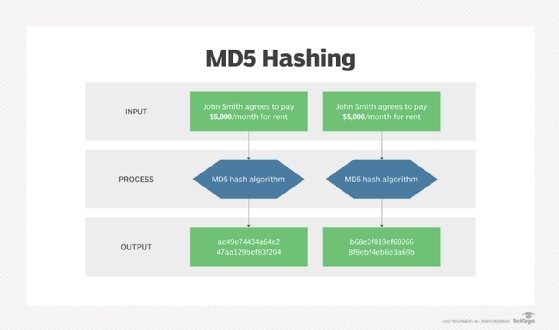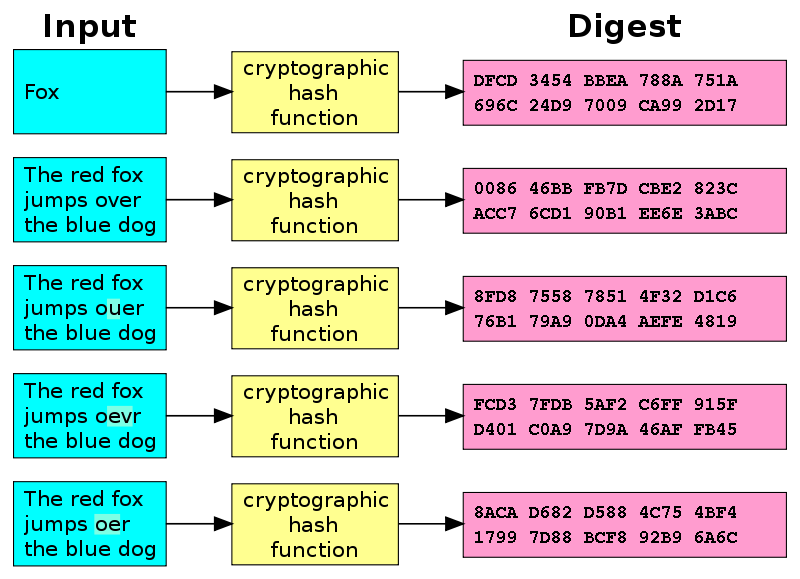
SOLVED: Using the following limited string of characters "abc123 ", create a "dynamic" rainbow table of all passwords 4-7 characters in length, along with the MD5 hash of each password. Store them

MD5SUM - Calculate and verify MD5 hash values for files. : Branko Lankester : Free Download, Borrow, and Streaming : Internet Archive

MD5 Generation Auto-Generated Slides To Visualize MD5 Hash Generation by Chris Fremgen. - ppt download